RPKI-IRR Hygiene in the RPKI Era
Note of paper “IRR Hygiene in the RPKI Era” (PAM ‘22)
Introduction
- IRR & RPKI
- Improve routing security in the Border Gateway Protocol (BGP) by allowing networks to register information and develop route filters based on information other networks have registered.
- IRR: 基于签名的系统,IRR的签名可以由任何人创建(lack of validation standards, not strictly validated)
- RPKI: 基于证书的系统,RPKI证书由根CA颁发
- Goal: Protect against unauthorized origin announcements (origin validation check)
- IRR and RPKI operate in parallel
- Telia Carrier (recently rebranded to Arelion), a participant of MANRS, helps its customers keep their IRR records current and drops all RPKI invalid routes [5]
- IRR is inaccurate due to improper hygiene (no penalty to the address space owner for not updating the origin information after changes in routing policy or prefix ownership)
- Increase inconsistency between IRR and RPKI
Background and Related Work
- IRR
- Use Routing Policy Specification Language (RPSL)
- mntner: contains authentication information required to create, modify, and delete other IRR objects
- aut-num: contains the name and routing policies of an AS
- route / route6: contain IPv4 and IPv6 prefixes and their origin AS information
- e.g., route: 137.110.0.0/16 origin: AS7377
- IRR mismatching information: 55% outdated (Khan, A Comparative Study on IP Prefixes and Their Origin Ases in BGP and the IRR, SIGCOMM’13)
- Use Routing Policy Specification Language (RPSL)
- RPKI
- ROA
- Format: IP Prefix, ASN, Max Length
- E.g., 137.110.0.0/16, AS7377, 20
- Format: IP Prefix, ASN, Max Length
- Misconfigurations caused invalid announcements decreased (Chung, RPKI is Coming of Age: A Longitudinal Study of RPKI Deployment and Invalid Route Origins. IMC’19)
- More transit and content providers had started to enforce RPKI-based filtering, and fewer illicit BGP announcements were propagating across networks. (Testart, To Filter or not to Filter: Measuring the Benefits of Registering in the RPKI Today, PAM’20)
- Caching servers of up to 20% of deployed RPKI RPs did not fetch complete or timely copies of RPKI data (Kristoff, On Measuring RPKI Relying Parties, IMC’20)
- ROA
Datasets
- Analysis of the causes of inconsistency
- CAIDA’s Inferred AS to Organization Mappings (as2org)
- authoritative IRR information
- Routeviews Prefix to AS mappings for IPv4 and IPv6 (pfx2as)
- AS Relationships
- AS Rank
- CAIDA’s Inferred AS to Organization Mappings (as2org)
- IRR datasets
- Routing Assets Database (RADB)
- RIPE IRR
- APNIC IRR
- APNIC IRR
- RPKI datasets
- RIPE NCC publishes daily validated ROA objects from all five RPKI trust anchors (APNIC, ARIN, RIPE NCC, AFRINIC, LACNIC)
- MANRS Participants
- Mutually Agreed Norms for Routing Security (MANRS) project publishes its list of participants on its website.
Methodology
- Classification of IRR records
- Consistent: Records that show full consistency in prefix and origin AS.
- Inconsistent ASN: The ASN in an IRR record does not equal that of the ROA.
- Inconsistent length: The ASNs are the same, but the prefix length differs.
- Not in RPKI: No corresponding prefix in the ROA
- Classification of ASes registered in IRR
- Entirely Consistent: All its IRR records are classified
- Entirely Inconsistent: either inconsistent ASN or inconsistent length
- Mixed: associated with both consistent and inconsistent IRR records
Prefix Origin Pair Consistency
- IRR & RPKI
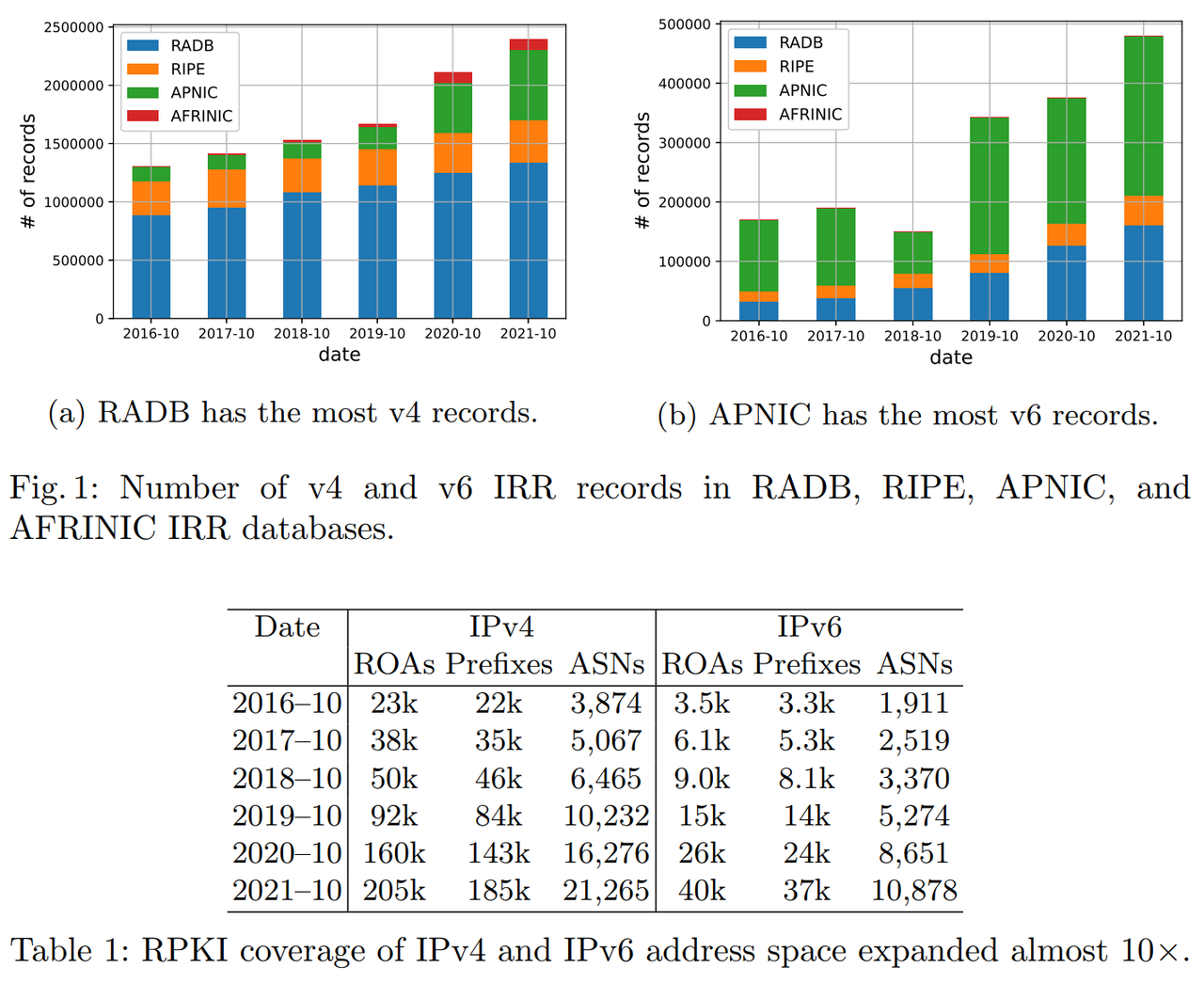
- IRR records >> RPKI records (nearly 10x)
- IPv4 vs IPv6
- RADB IRR: 28.3% matching ROA
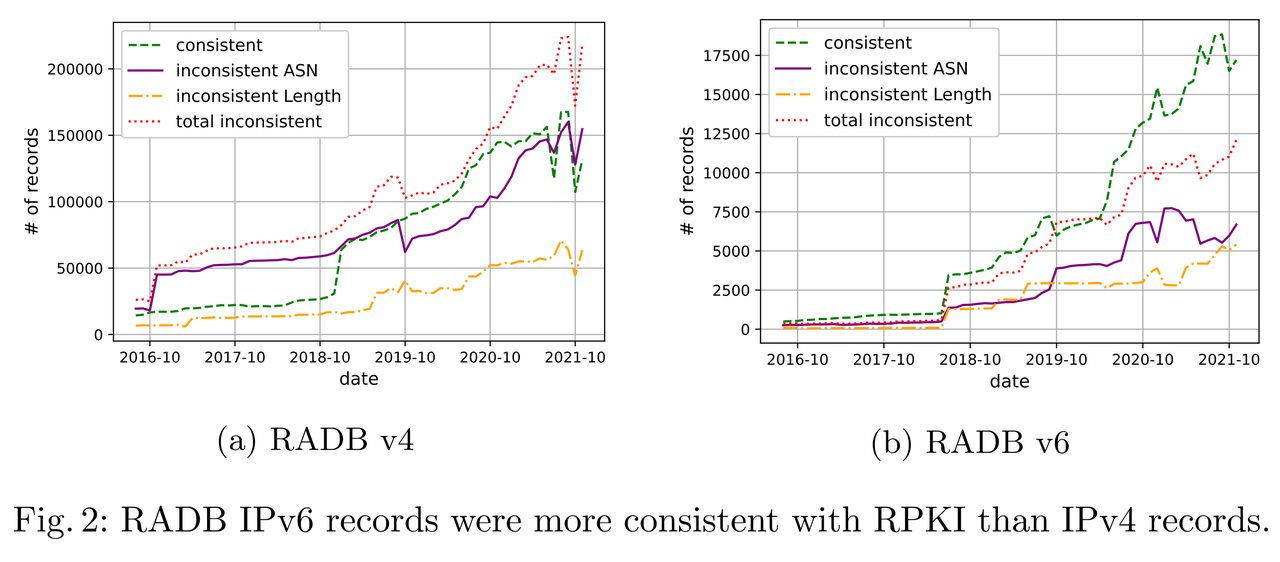
- Oct. 2021: RADB IRR dataset (v4, 21% has corresponding ROA): 38% consistent, 46% inconsistent ASN, 16% inconsistent length
- RIPE IRR: 45.2% matching ROA
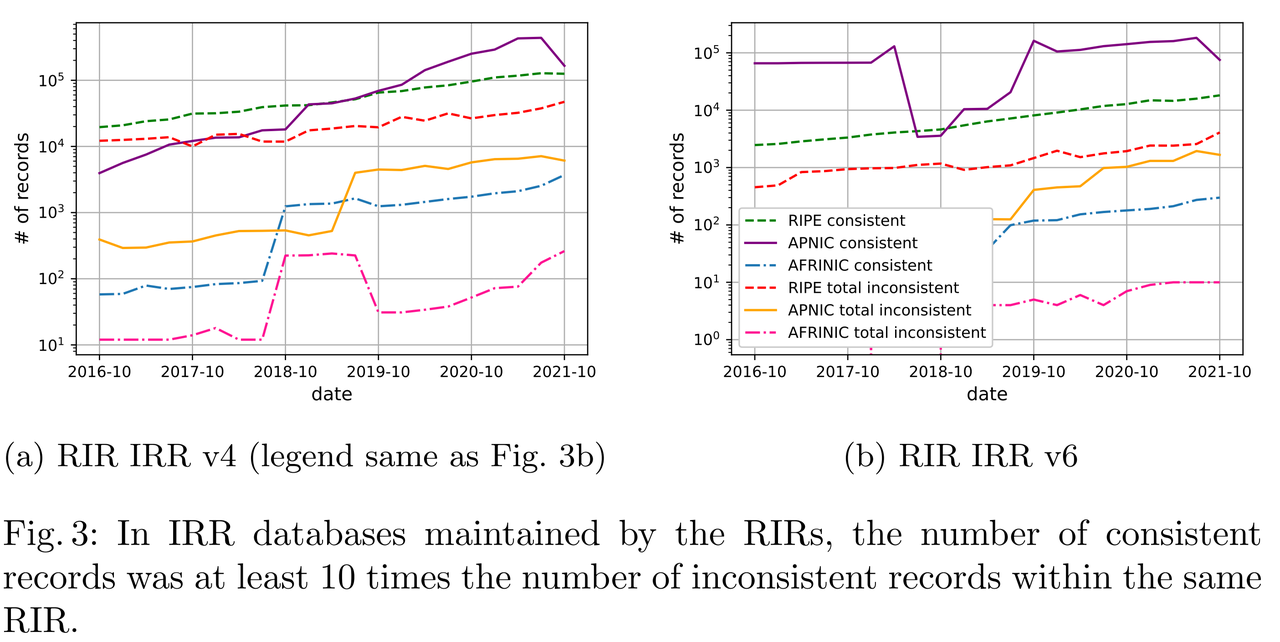
- RIPE IRR has better-maintained records
- APNIC IRR: highest consistency with RPKI
- The IRR databases operated by RIRs showed higher consistency with RPKI compared to RADB
- RADB IRR: 28.3% matching ROA
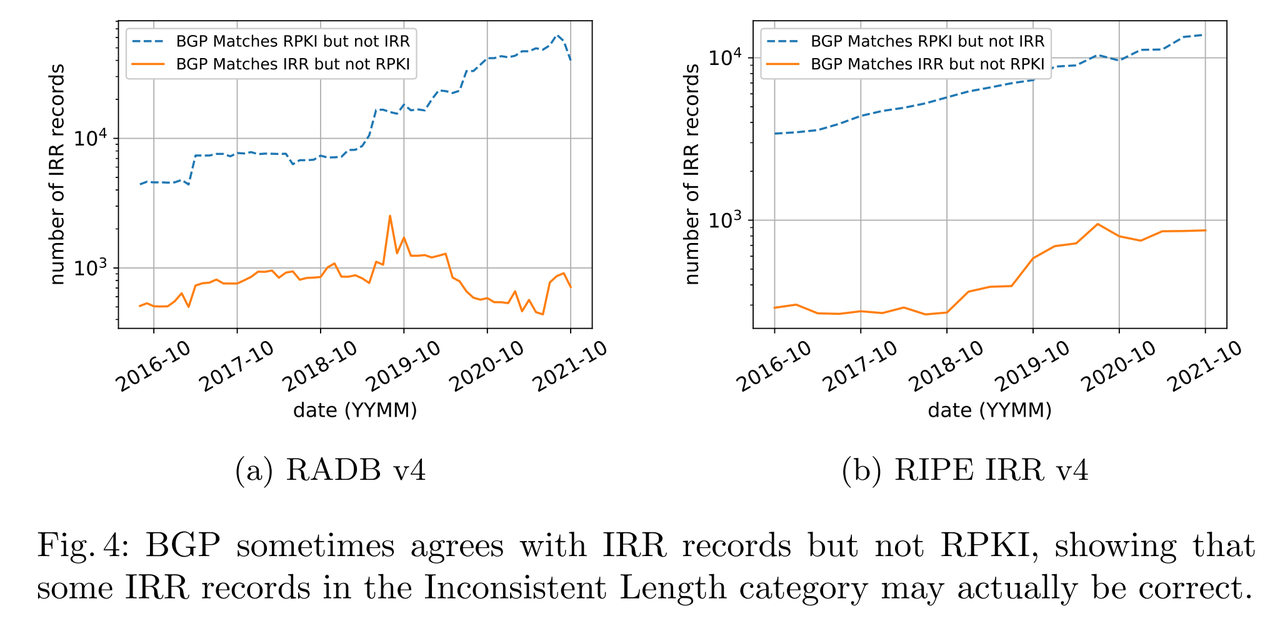
- Causes of Prefix Length Inconsistency
- RPKI misconfiguration
- To find out whether the networks registered inaccurate IRR records or incorrectly used the RPKI Max Length, we compared the inconsistent length records to their BGP announcement and corresponding RPKI ROAs.
- Analysis of ASN Inconsistency
- Conflicts: any two IRR records with the same IP prefix but different origin ASes.
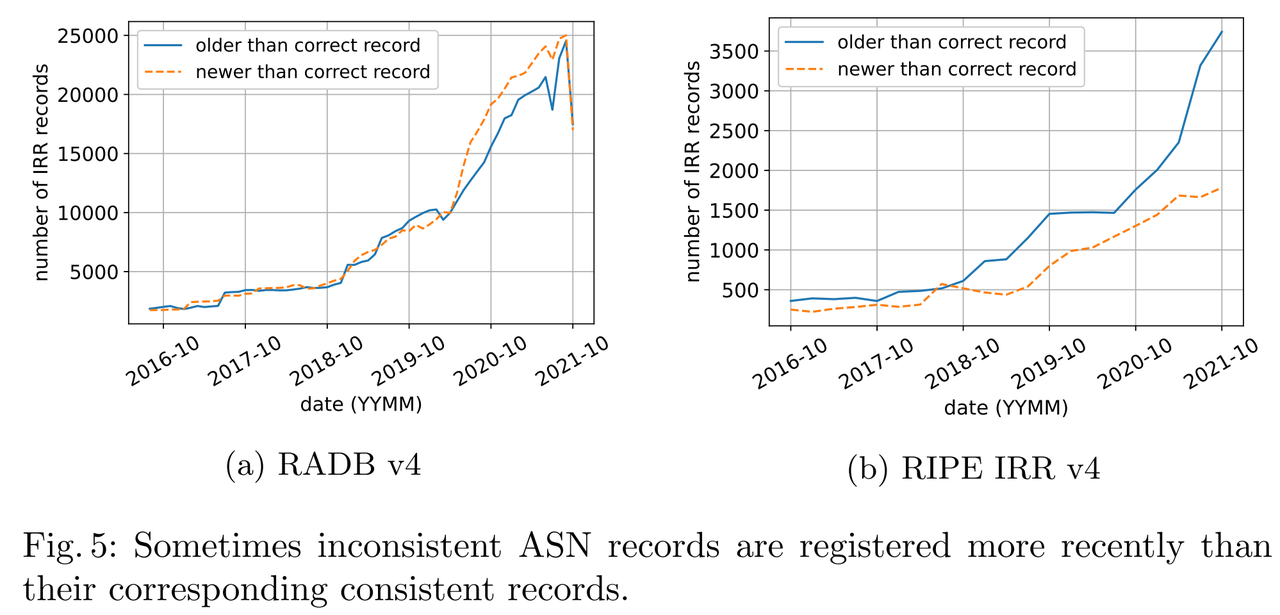
- This result contradicts the intuition that an inconsistent ASN record should be older than its correct counterpart because inaccurate IRR records are likely stale.
- Providers could proactively require their customers to remove their IRR entries upon reclamation of address space to promote good IRR maintenance
- Conflicts: any two IRR records with the same IP prefix but different origin ASes.
ASes behind IRR inconsistency
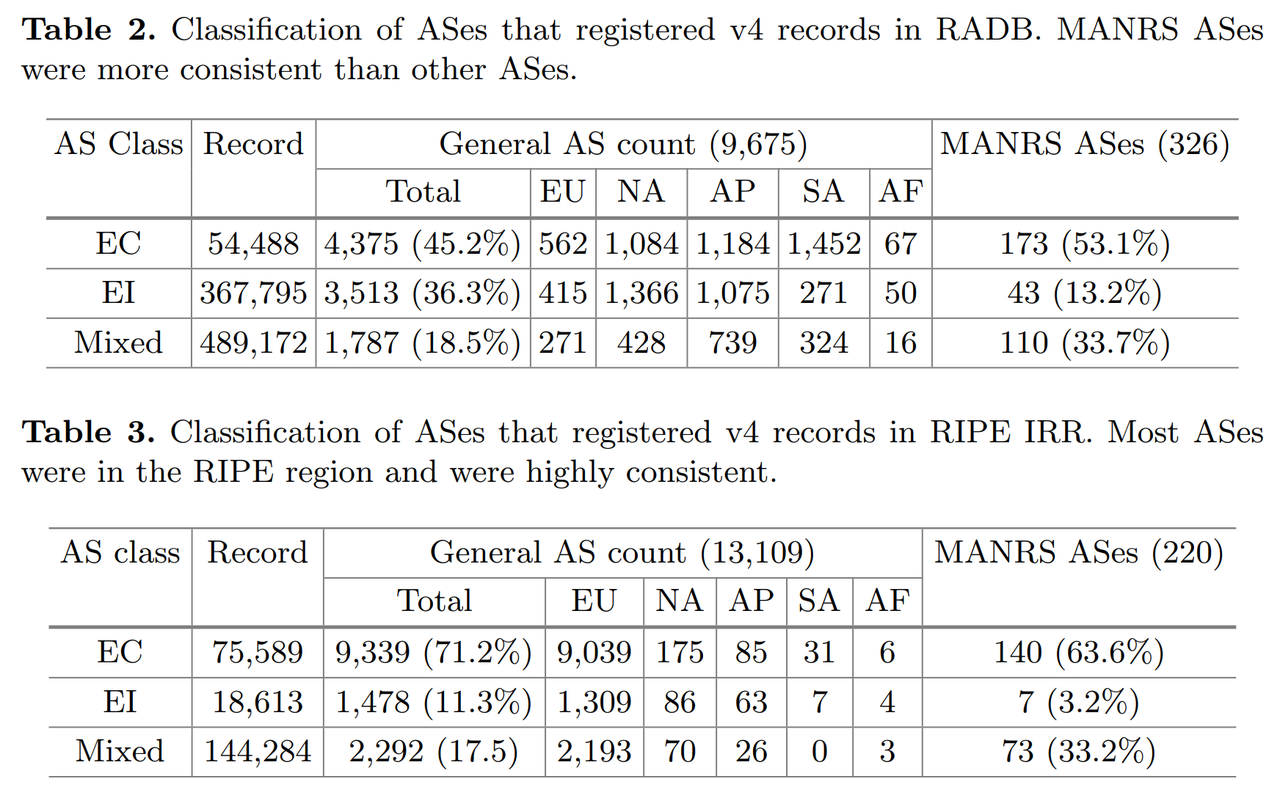
- Table 3 shows that the authoritative RIPE IRR had few users outside of the RIPE service region, and the ASes had good IRR hygiene as a result of the validation requirement of the RIPE Database.
Summary and Future Work
- The future of IRR can be promising, as new tools such as IRRd Version 4 have been developed to help operators automatically validate IRR information against RPKI. This could further improve the accuracy of the IRR and contribute to better routing security.