ZKP学习笔记
ZK-Learning MOOC课程笔记
Lecture 11: From Practice to Theory (Guest Lecturer: Alex Lombardi)
11.1 The Feasibility of Interactive ZK
- SMPC: semi-honest protocol + ZKP = malicious protocol
- Parties use ZKP to prove that they follow the protocol
- Theoretical Research on Cryptographic Proofs
- Feasibility (do they exist in principle?)
- SNAR(G/K)s, other protocols (ZK, WI, WH, etc.)
- Strong attack models (Concurrent? Quantum?)
- Minimize Assumptions (to the extent possible)
- Trusted setup (CRS/URS/plain model)
- Security reduction based on simple, well-studied, falsifiable assumptions. Improve efficiency
- Amount of communication, number of rounds
- Prover/verifier efficiency
- Feasibility (do they exist in principle?)
- Example: Interactive ZK
- No trusted setup allowed: Security against Malicious verifier is hard to guarantee.
- ZK for NP [GMW86] with inverse poly soundness error.
- Optimization
- Sequential repetition works (but very inefficient).
- Parallel repetition reduces soundness error but may not preserve ZK
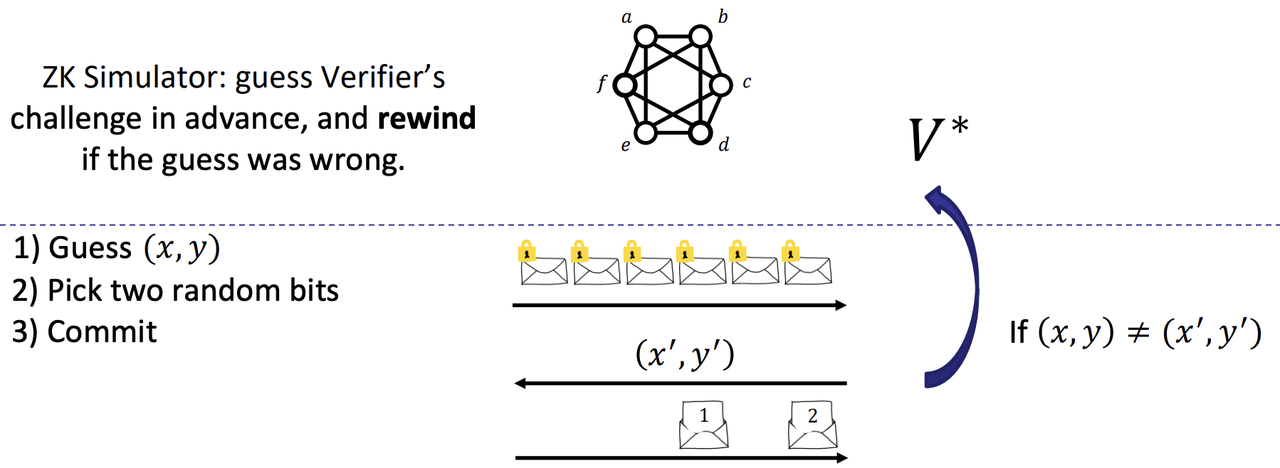
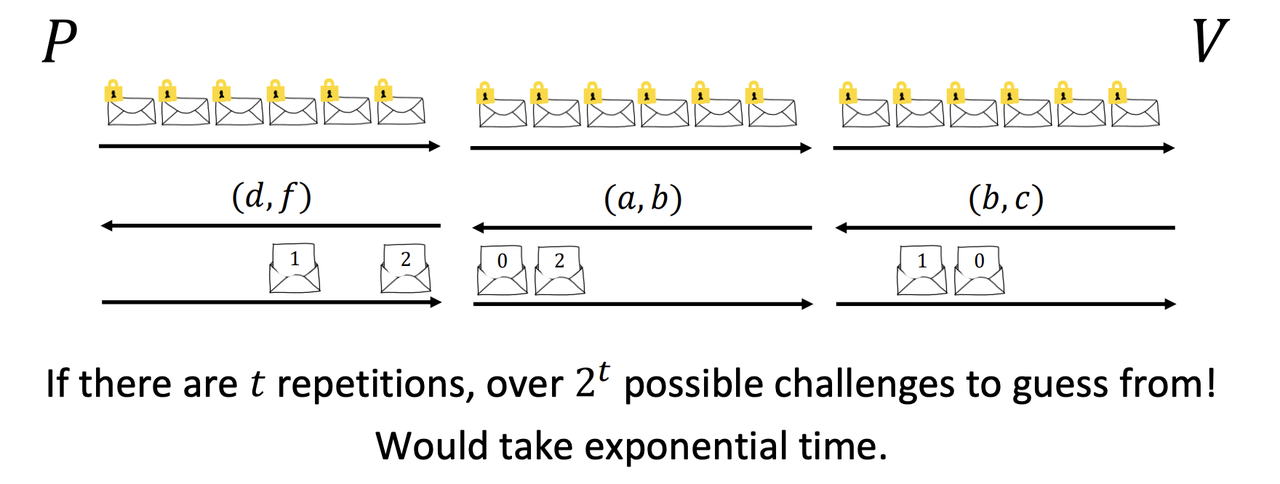
- [DNRS99]: If you can do Fiat-Shamir for $\Pi$, then $\Pi$ wasn’t malicious-verifier ZK.
- Many lines of research devoted to understanding the feasibility of interactive ZK.
- How many communication rounds? [BKP18] suggests that you can do it in 3.
- How efficient can you make the prover? [IKOS07, …]
- Stronger forms of security: quantum attacks, concurrency