MIT IAP 2023 Modern Zero Knowledge Cryptography课程笔记
Lecture 5: Commitment 2 (Ying Tong Lai)
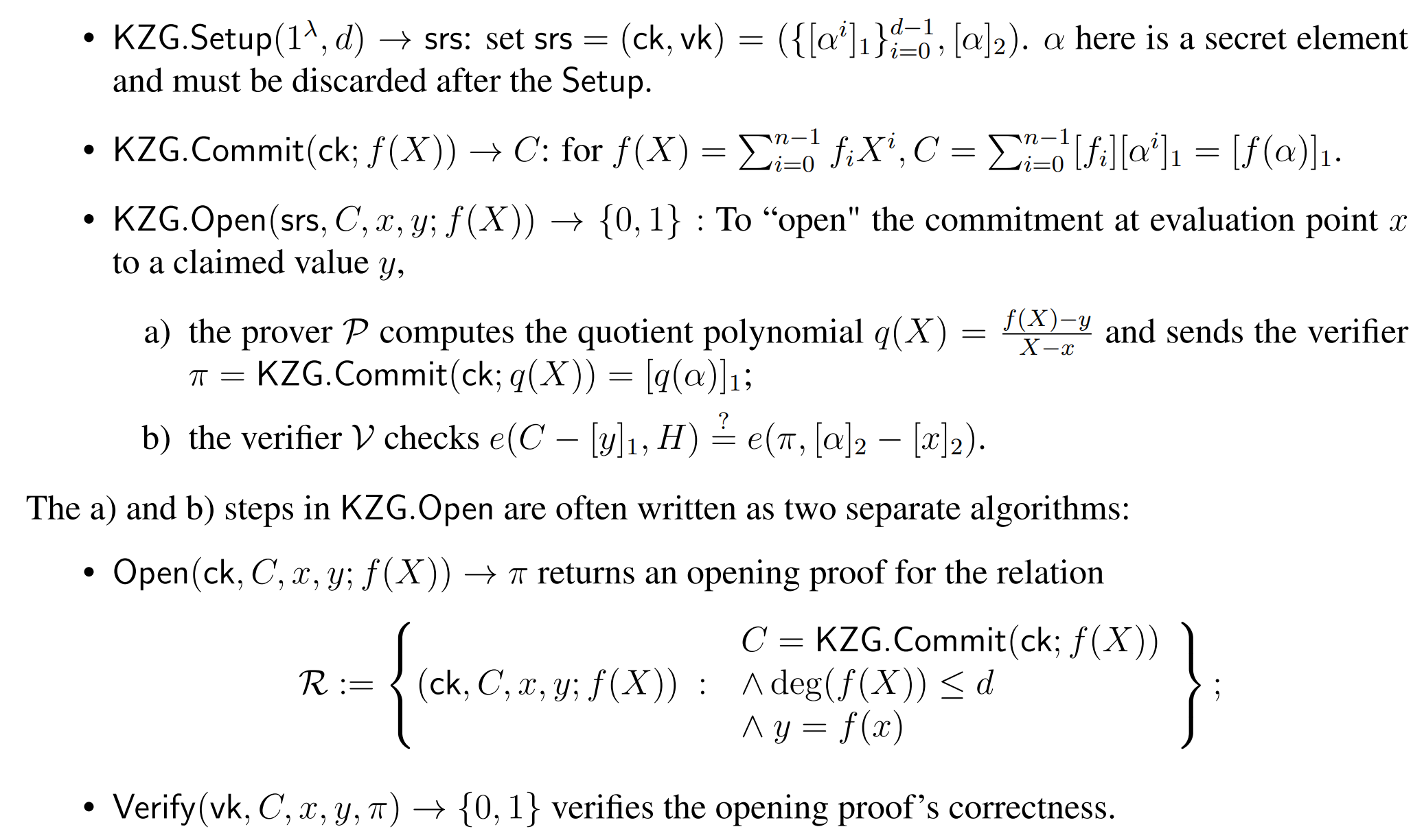
- Polynomial Commitment
- f(x) = $a_0$ + $a_1x$ + $a_2x^2$ + $\dots$ + $a_nx^n$
- $a_i$ is secret
- commit(f,z,y) = C
- The commitment proved that
- f(z) = y
- C is the commitment of f
- KZG commitment scheme. It is used in protocols like Sonic, Marlin, and PlonK. (Marlin and PlonK improve on Sonic by constructing a different polynomial IOP.)
- How to generate $\tau$ (trusted setup)
- Multiple-party computation
- Each party generate a random beacon
- Aggregate all beacons as $\tau$
- No one knows $\tau$ exceplt compeletly collusion
- Multiple-party computation